Briefly, a Network is at least 2 computers (or associated pieces of
technology) connected together for the purposes of sharing resources
that might otherwise be under-utilized. Networks are also used for connecting
people to other people for collaborative tasks.
Resources made available via a network may include:
- Secondary Storage: hard disks, tape drives etc.
- Attached Peripherals: printers, scanners, modems, CD-ROMS....
- Administration Personnel: many networks allow access to diagnostic
routines and procedures, help systems and operator controlled technical
assistance.
- Communications: most networks allow machine-machine communication,
including e-mail, messaging, video links, teleconferencing etc.
Networks exist in the most unlikely places. In the era of the 'no
computer' computer, we see networks extending to control the family
car (the 1998 BMW had a 6 processor network controlling the many electronic
features of the car - mechinics log on to the network to ask each
of the systems how they are), Busses and Taxis, and even the fridge
(a japanese invention sees the Refrigerator connected to the Internet,
monitoring and ordering goods used).
Terminology
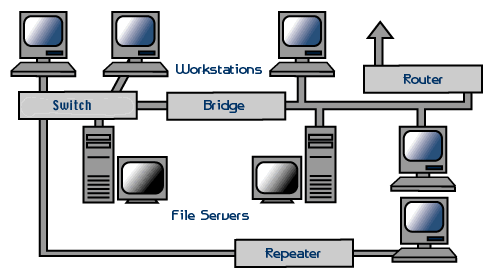
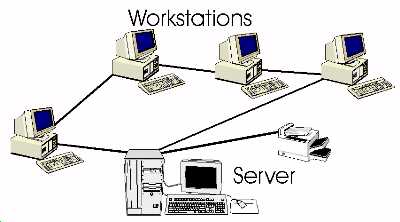
A Network physically comprises, usually, a collection of WORKSTATIONS,
network cabling, may include a SERVER and attached DEVICES. Controlling
the interaction of these components is a NETWORK OPERATING SYSTEM (a
collection of specialised programs).
Each workstation usually has a NETWORK ADAPTER which manages signal
propagation and signal reception for the workstation.
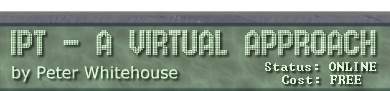
CLIENT SERVER networks usually involve a main computer that
acts as the main storage area for data, and usually stores much of the
software used on the workstations. Workstations are connected to this
server (via a number of different topologies), and under the
supervision of the network operating system are able to access the resources
stored there.
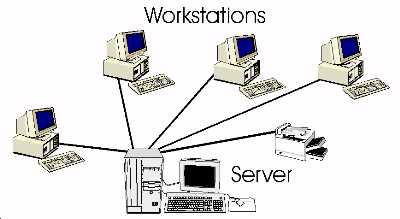
PEER TO PEER networks usually involve each of the workstations cooperatively
sharing data, peripherals and software, with no central server. Each
peer shares responsibility for maintaining the network, and as such
acts like both a workstation and a server in it's own right.
Client-server networks rely on the server's presence - should it crash,
much of the resources are no longer available to the client workstations.
In a Peer-to-Peer network, since no one workstation is centrally responsible,
the loss of a workstation (due to a crash) results in only the loss
of resources directly connected to it, the network usually is still
able to function.
Media and Signalling
For successful network communication, you need a means of transporting
signals (digital or analogue) between workstations, and some device
that can propagate (or send and recieve) the signals.
Some networks use UNGUIDED media - broadcast TV, microwaves, infared
and radio waves are considered unguided - the signals are BROADCAST
in the general direction they need to travel (and may use atmospheric
or other conditions to 'bounce' signals to roughly where they need to
go).
GUIDED MEDIA networks include those that use UTP (Unshielded Twisted
Pair copper wiring), Fibre Optic cables, coaxial cables etc. These are
point to point connections, and are often more reliable than unguided
media (but more expensive to install)
Signal propagation is usually handled by the NETWORK ADAPTER (or NIC
= Network Interface Card).
Different networks use different TRANSPORT PROTOCOLS, with many relying
on successful transport of PACKETS of data. A typical packet might contain
some or all of the following information (although not necessarily in
this order):
- Header Bits (signalling the beginning of a packet)
- Address information
- Senders address
- Receivers address
- Integrity checking information (to allow the detection of errors
in the packet caused by transport)
- A Sequence number (so the receiving device can reconstruct the order
of arriving packets)
- The data (usually in manageble 'chumks', like 1024 bits)
- Encryption information (If the data is sensitive, it may be sent
encoded, and will need to be decoded on receipt)
- End bits (to signal the end of a packet)
In large networks (like the telephone network), packets may not all
travel the same route (ie. they may use different paths to get to the
same place), so the sequence number can help the receiver re-assemble
the data
ATTENUATION refers to deterioration of signal quality due to interferance
or distance. Should the data need to travel over large distances, to
prevent signal loss REPEATERS are used - these boost the signal strength
making the transport distances potentially limitless. Nearly all network
adapters have inbuilt repeaters to ensure the highest quality signal
propagation.
Client-Server Networks typically use NETWORK HUBS to provide central
points of connection to the server. The hubs usually have one fast connection
to the server, with workstation network cabling connecting into the
hubs.
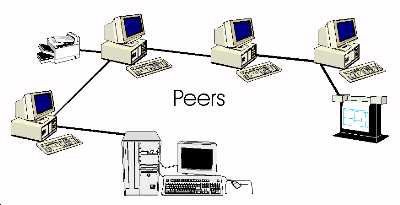
Topology
The TOPOLOGY of a network refers to the LOGICAL layout
of the Workstations (and server if there is one). Ther topology can
often differ from the visible wiring pattern.
Each workstation on a network typically has a unique ID - this allows
packets to be addressed to individual machines on the network. It is
usually possible to send to individual workstations, as well as groups
of workstations using these ID's.
Star Topology

In a STAR network, each workstation is connected to a common
switch (say, a bank of hubs). When one workstation sends a message to
another, the message is first sent to the common switch, and then routed
from there to the appropriate destination workstation. The switch decides
who recieves the packets of data depending on the addressing information
attached to that packet.
Should one workstation crash, the rest of the network is largely
unaffected, unless someone attempts to signal the 'missing' workstation
or access resources attached to it. Clearly, if the Server or switch
fails, the network also grinds to a halt.
It is possible for more than one message to be routed through a star
network at one time - thus these styles of networks tend to be faster
than those that follow.
Bus or Ring Topology
Both the BUS and RING topologies are BROADCAST NETWORKS
- that is, when one machine wishes to send packets to another machine,
everyone gets a copy of the packets, and all but the TARGET machine
discards them
Use of the network is often controlled by a scheme similar to a central
DATABUS - ie. the workstations take turns of being allowed to
access the network, when they have had their 'turn', they pass a TOKEN
code to the next machine in line. Ownership of the token means
it is your turn to use the network.
With RING topology, the network wiring forms a LOOP, so that
signals travel around the loop in one particular direction, as does
passing the token.
With BUS topology, the network is layed out in one long line.
When signal generation occurs, signals are sent from the sending machine
two ways - towards both ends of the network where they are absorbed.
Workstations using BUS topology listen to the network line until
there is no traffic, then begin signalling. Occasionally, workstations
will begin signalling at the same time - a collision or contention
then occurs, is detected, and then each of the workstations wait a random
time delay before trying again to signal.
Thin Ethernet is a common application of a BUS topology that uses a
contention scheme
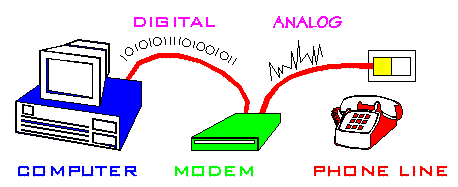
The Telephone Network - PTSN
(Public Telephone Switched Network)
The telephone network is one of the few trully ubiquitous networks
(ie. it connects to nearly every place on the globe). Originally an
analogue network (transmitting sound as waves of varying intensity),
these days most of the telephone network is digital.
Your handset collects analogue information (your speech) and transmits
it to your local exchange via UTP cabling (copper wires). At the exchange,
analogue id converted to digital, wrapped up into packets (containing
about 1024 bits of data each + control information) and then routed
via FIBRE OPTIC CABLE to the destination exchange.
The paths that packets may take can be incredibly varied and scenic.
At the destination exchange, the control information is stripped off
the packets, they are then re-joined in the correct sequence, converted
into analogue, and pumped to a handset through copper wire at the other
end - emerging once again as sound.
The telephone network is incredibly flexible and robust - allowing
the transmission of all sorts of data (from FAX streams, ATM transactions
to primitive VIDEO CONFERENCING)
The PTSN has a maximum BANDWIDTH of about 5Mb/s
The Telephone Network - ISDN
(Integrated Services Digital Network)
The IDSN is a high speed DIGITAL service that avoids the need to convert
analogue to digital and back again. Using dedicated phone lines, it
is possible to plug digital devices directly into ISDN lines, which
provide a much greater bandwidth (100Mb/s and beyond)
Whilst still in it's infancy, ISDN services will play an important
part in the replacement of the PTSN, as user demand for more and more
services reequiring highr and higher bandwidths emerge.
The Internet
The INTERNET is a collection of COMPUTER NETWORKS from AROUND THE WORLD
connected together and able to exchange information of various types.
This data exchange is possible because all connected computers on the
'Net use the same method of data transfer (TCP/IP - Transport Control
Protocol/Internet Protocol) allowing relatively fast platform independent
communications.
The Internet is everywhere and nowhere. It arose from a number of educational
and military networks, as was modelled on a distributed computing model
- no one computer on the Internet is centrally responsible for it. With
so many computers and network paths for data to travel through, if one
computer or network ceases to function, the data can be automatically
routed via another path.
The internet is comprised of Mainframes, Mini computers, humble PC's
and Mac's on people's desktops. It is largely uncensored and open, pervasive
and growing. Built to use existing network infrastructure (the global
telephone network), the protocols in place are sufficiently robust to
ensure error free transmission across the planet in under 1/2 a second.
Originally only ACADEMICS and MILITARY used the Internet - they established
a need to communicate between networks. Now, all sorts of people from
Educators, Business People, Students, Politicians, and Librarians (Cybarians)
use the 'Net
The Internet of today makes available a VAST collection of resources
and services make the 'Net an attractive place to graze. More importantly,
it provides a global medium for people to communicate with other people.
As a rich resource base, means of communication and recreational vehicle,
cyberspace is a fun place to visit (so long as you don't live
there) - the 'CDROM' in the sky is a poor analogy - as anyone can publish
and share their ideas, the amount of content is growing at an unprecedented
rate. The quality and veracity of that content is more of a problem.
How to Get Connected:
A 'dial-up' connection
Most home users can buy time from an Internet Service Provider
(ISP). ISP's own computers that are (usually) connected to other computers
that have fast (high bandwidth) connections to the major Internet backbones
that criss-cross most countries these days. The range of deals
is wide, and the charging structures vary from ISP to ISP.
Some accounts are time/volume charged, some have small amounts of connection
time per week, others are charged Annually, others Monthly
Terminal Connection
Shell accounts and other TEXT based services were the most comon form
of Internet connection as recent as 6 years ago. Graphs were available,
but had to be downloaded separately using a command line command.
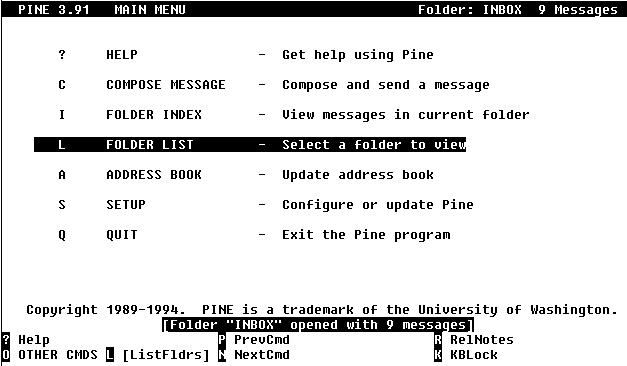
E-mail using PINE
Electronic Mail (or E-Mail) remains one of the most
used services available throught the Internet. E-Mail, like normal
(Snail) mail involves people composing messages to other people,
addressing them (an email address like pwhitehouse@optusnet.com.au
follows a general pattern or username@hostname) and sending
them off to find their own way through the network. E-Mail can be
read, replied to, forwarded and redirected.
A relatively recent addition to the services available
through the Internet is the World Wide Web. First prototyped by Tim
Berners-Lee, the www uses a special protocol to transmit web pages
(HTTP = Hypertext Transport Protocol) that can include text, pictures,
links and other interactive media.
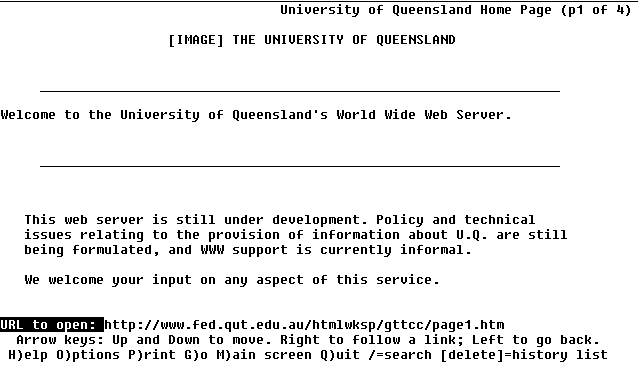
World Wide Web browsing using LYNX
The World Wide Web is accessed through a Browser (reading this text
book means you are already using a browser - either Netscape, Internet
Explorer or one of the less common browsers). Originally, a browser
could only view web pages. These days, most of the Internet's services
can be acessed through your browser using plugins and helper programs
Internet Services
The World Wide Web
Usually 1 Way Communication - you browse collections
of grapically displayed resources (including Text, Pictures, Video,
animations, Sound FX), navigating with the use of LINKS
Typically, WWW browsers are converging many services available
on the 'Net into the one interface - they can be colorful, intuitive
and fun to use.
Typically the WWW is navigated one of three ways:
- Browsing (not sure what you want nor where it is located)
= wandering around, following interesting links until you arrive at
a suitable destination
- Searching (know what you want but not where it is)
= using search engines to locate resource
- Bookmarking (know what you want and where it is to be
found) = jumping straight there with the aid of a bookmark
placed during a previous visit
E-Mail
2 Way Communication 'delayed' where you send and recieve electronic
mail, forward it, store it, reply to it and so on.
E-mail relies on knowledge of e-mail addresses, it is a less
formal way of communicating with other people than say a physical letter
to someone. E-Mail communication is effective if it is checked often
and replied to as soon as possible.
FTP (file transfer protocol)
Usually 1 Way Communication - you LOG IN to remote computers
and transfer files from there to you or from you to them.
You typically need to know the name (or IP address) of the computer
you wish to get files from (dingo.cc.uq.oz.au or 130.12.128.43 for example),
as well as the directory and file name of that which you want (e.g.
/a/long/and/complicated/path/file.doc)
Gopher
1 Way Communication - you navigate MENUs searching for
topics of interest, then either read or e-mail yourself the results
of the search
Newsgroups (Usenet)
2 Way Communication 'delayed' - you browse posted E-Mail
notes on world wide notice boards, post your own messages and reply
as you see fit.
IRC (Internet Relay Chat)
2 Way Communication 'live'- you join discussion groups and chat
online (via keyboard).